Monitor & Alert for Failed Authentication Attempts to Your AWS Account

We live in the information age. In a world where knowledge is power, your data is the most precious commodity. This makes your data stores very lucrative targets for attackers all around the world. If you’re hosted on AWS, there are many measures you can employ to keep your data safe. This article describes one such measure.
The internet today is scouring with automated bots looking for anything they can attack. Some love login pages & spend days trying to brute force their way into the site until either the server shuts them out or they get in! Others simply search every line of code ever committed to any public GitHub repository looking for keys & credentials that someone might have pushed to their Git repo accidentally.
If you would like to see this live just launch a public EC2 instance & wait. Within minutes, you’ll see all kinds of internet traffic hitting your instance. Even though you haven’t touched the instance, you didn’t even try to log into it, neither is it running anything like a web server, it still attracts all this strange traffic from all over the world. These are mostly bots trying to get in, hoping they’ll find something of value. Sure there are patterns in the traffic (like their countries of origin) that might intrigue some researchers, but that’s a topic for another day.
Monitoring AWS Login Attempts
Our objective in this article is to build a system that can monitor for & alert us about failed attempts to log into our AWS account. Here is what we will be building:
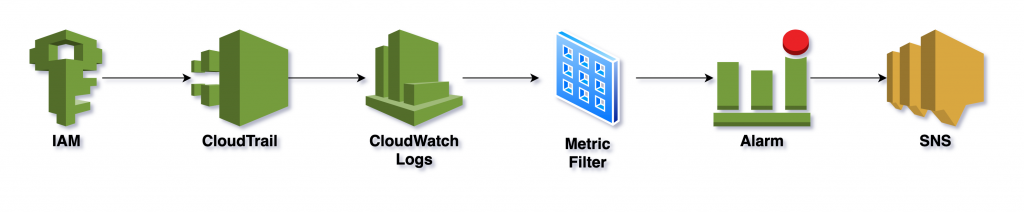
Here’s how it works:
- CloudTrail is continuously logging all AWS activity, including login attempts, to CloudWatch Logs.
- A metric filter in CloudWatch Logs is continuously looking for patterns in the log that indicate failed login attempts.
- When the filter finds a match, it increments the count of a custom metric we created.
- When the metric crosses a threshold, we get an alarm!
Now let’s build this, shall we?
Create CloudTrail Trail
First, create a CloudTrail trail. Open console.aws.amazon.com/cloudtrail/home#/create, provide a trail name & an S3 bucket. Enable CloudWatch Logs & provide a log group & an IAM role.
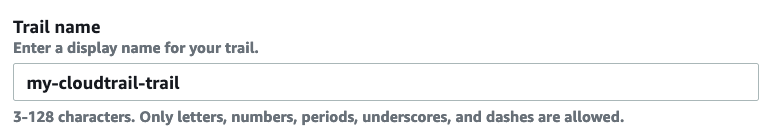
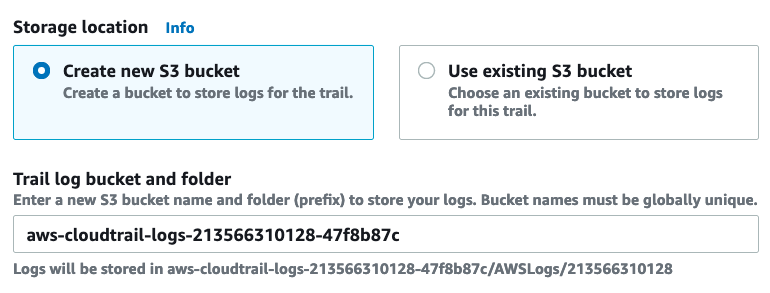
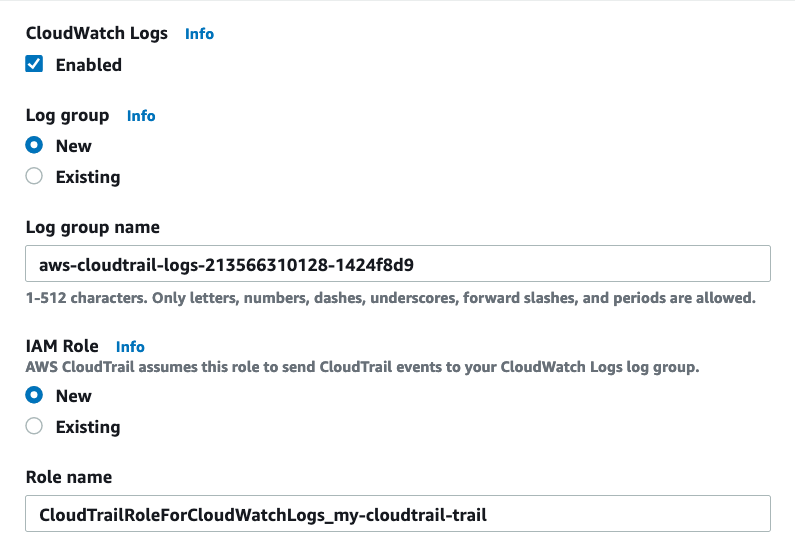
Leave all other settings to their defaults & finish creating the trail.
Test CloudTrail Trail
Open a private window in your browser & try to log into your AWS account with an incorrect password. One attempt is enough. Both the root account & IAM users are acceptable here & the presence or absence of MFA doesn’t matter. If MFA is enabled, enter an incorrect code there as well. Now close the private window & wait.
Sometime in the next 15 minutes, the failed attempt should show up at console.aws.amazon.com/cloudtrail/home#/events?EventSource=signin.amazonaws.com&CustomTime=1800000. Open the event & you should see an event record like this:
{
"eventVersion": "1.08",
"userIdentity": {
"type": "Root",
"principalId": "123456789012",
"arn": "arn:aws:iam::123456789012:root",
"accountId": "123456789012",
"accessKeyId": ""
},
"eventTime": "2021-03-21T06:49:35Z",
"eventSource": "signin.amazonaws.com",
"eventName": "ConsoleLogin",
"awsRegion": "us-east-1",
"sourceIPAddress": "303.310.353.332",
"userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.16; rv:86.0) Gecko/20100101 Firefox/86.0",
"errorMessage": "Failed authentication",
"requestParameters": null,
"responseElements": {
"ConsoleLogin": "Failure"
},
"additionalEventData": {
"LoginTo": "https://console.aws.amazon.com/console/home?state=hashArgs%23&isauthcode=true",
"MobileVersion": "No",
"MFAUsed": "Yes"
},
"eventID": "e57a2dc5-f472-4557-9e93-6314816e29be",
"readOnly": false,
"eventType": "AwsConsoleSignIn",
"managementEvent": true,
"eventCategory": "Management",
"recipientAccountId": "123456789012"
}Notice the errorMessage is set to Failed authentication. We’ll use this later.
Create CloudWatch Logs Metric Filter
Head on over to the CloudWatch Logs log group for the CloudTrail trail you created earlier & select “Create metric filter” from the Actions menu. Provide the following filter pattern:
{ $.eventSource = "signin.amazonaws.com" && $.errorMessage = "Failed authentication" }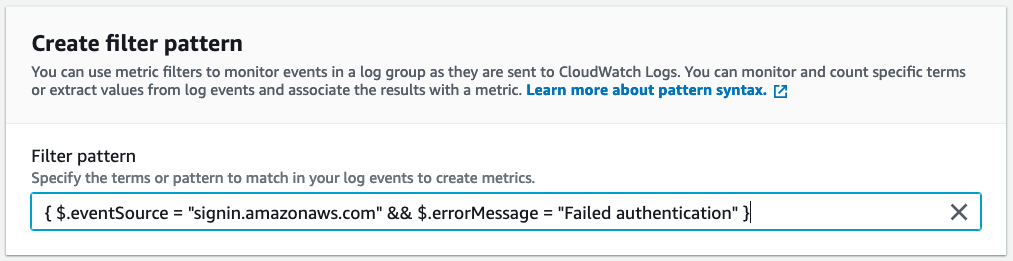
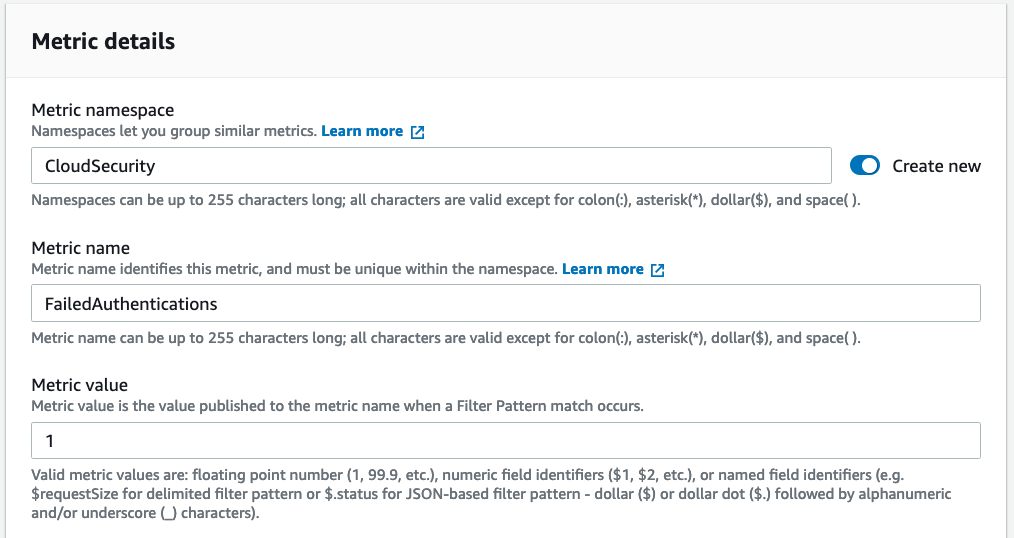
CloudWatch Alarm & SNS
The rest of the workflow is pretty standard. Create a CloudWatch alarm for the custom metric that you created above. Create an SNS topic & send the alarm notifications there. You can then subscribe to the SNS topic with email, SMS, etc.
About the Author ✍🏻

Harish KM is a Principal DevOps Engineer at QloudX. 👨🏻💻
With over a decade of industry experience as everything from a full-stack engineer to a cloud architect, Harish has built many world-class solutions for clients around the world! 👷🏻♂️
With over 20 certifications in cloud (AWS, Azure, GCP), containers (Kubernetes, Docker) & DevOps (Terraform, Ansible, Jenkins), Harish is an expert in a multitude of technologies. 📚
These days, his focus is on the fascinating world of DevOps & how it can transform the way we do things! 🚀





